
Cybersecurity in business (+pl)
Opublikowano: 3 września 2015
(polska wersja – str. 2)
Public access, ease and comfort of use, as well as rapidly growing amount of processed information are the main reasons behind the need to continuously develop modern technologies, which have an increasingly significant role in facilitating key business processes. This situation has inherently lead to a hike in the number of cyberthreats, a thorny topic as of late, as cyberthreats pose a risk to the image of any organisation and make companies susceptible to serious financial losses.
The target of cyberthreats
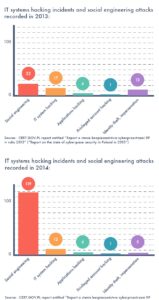
There has been a great deal of data regarding cyberthreats. When comparing CERT (Computer Emergency Response Team) reports on the state of cyberspace security in Poland in 2013 and 2014, one will find out that in 2014 the number of IT systems hacking incidents was lower than in the previous year. However, the number of social engineering attacks has increased – and almost five-fold. This state of affairs should lead to relevant lessons and some radical changes in the approach to security in view of cyberthreats. On the top of investing in network and systems protection, appropriate care must be taken to create staff awareness and build resistance to cyberthreats, both on the technology and the human level.
Media more and more often report on incidents relating to cyberattacks triggered by lack of employees’ awareness. In May this year, for example, we heard the story of a public administration office losing PLN 4m after paying the sum for a service into an account
belonging to fraudsters disguised as the service providers. The public officer deceived by the imposters was consequently subjected to disciplinary action and dismissed. Similar events took place in many other public finance institutions, just to mention hacking of the IT system in a town hall, as a result of which over PLN 940 thousand was embezzled. The number of incidents related to cyberthreats in private companies, such as accounting firms or legal offices where vast amounts of sensitive data gets stolen, has also consistently been on the rise. The scale of recent events is the confirmation of the fact that human factor is the weakest link in the security system.
Any organisation that gathers, processes and sends data can be affected by this issue. Each company that deals with electronic data management faces cyberthreats, no matter what the type, the utilised systems and applications complexity, or the number of staff are. These are employees, average users in the digital world unaware of existing dangers, who make it possible for hackers to launch successful attacks. Phishing is on of the types of attacks on an
individual employee. It consists of a user’s identity theft which leaves the victim potentially becoming a crime accessory or unintentionally putting the whole organisation in jeopardy.
Sometimes even apparently insignificant actions might have serious consequences. One thoughtless move, opening an untrusted email message, clicking a bogus link, a lost memory
drive – all can lead to enormous damage, not easy to undo, or often – irreversible. A single leak of sensitive information or a theft of intellectual property can cause work dismissals, losing
credibility in the eyes of stakeholders or loss of competitive position and, in turn, even bankruptcy of the organisation which is not able to regain the trust on the marketplace. It often stems from an attempt to conceal the details of the incident from the market and the organisation’s management, the decision ever more catastrophic as it disables the people in charge from acting in time, which then results in even worse situation of the entity in question.
How to protect yourself from a cyberattack?
A perfect method of protection does not exist, just as there is no 100% certainty that we ourselves will not become the target of an attack. It is very difficult to monitor and eliminate
internal and external threats which keep evolving and become more complex. Nevertheless, lack of activity, inertia based on denial that the risk exists, will sooner or later have results difficult to neutralise.
In order to protect oneself from threats in cyberworld, there need to be some actions taken by the entire organisation. The responsibility for the protection of information lies in the hands of all employees. Yet, for this responsibility to be clear and not merely assumed, the
management need to conduct a threats analysis and define the way of handling identified risks by pointing out which risks should be avoided, which ones accepted and which ones can be shared, e.g. with an insurer. The process of identification and management of incidents, where the focus is on the time when an event is raised and the speed of reacting to incidents, is equally important. Relying solely on IT systems administrators and IT specialists is intrinsically a philosophy set to fail.
Independent supervision and control are a fundamental element of management process. Without them, blind trust and wishful thinking are the only remaining options. Or even worse – the belief that the problem does not concern us. It does – it concerns everyone, no exceptions. Along with technological security systems, an ongoing practice of educating staff and of raising awareness should be an inherent element of management process in organisations. The efficiency of traditional security methods, such as protecting IT infrastructure with anti-virus software or firewalls, is limited if staff do not realise what kind of danger looms in cyberworld. The rules of management, protection and transmission of data based on the information security strategy need to be implemented and preceded by relevant staff training, so that employees understand and comply with safety measures and the management team be able to ensure these measures are adhered to. It is worth stressing out that the management team themselves should lead by example – personal engagement has a major effect on making sure staff awareness programs are fully effective.
Key elements in regard to cybersecurity management:
- Information management strategy – fully implemented and communicated to staff
- Analysis of risk arising from cyberthreats and plans for handling risk
- Developed and effective process of raising and management of security incidents
- Repeated training sessions and raising staff awareness
- Regular security audits, the results of which are addressed to the most senior management
Wioleta Bartczak, Security audit specialist at IMMUSEC,
Certified information security management systems auditor.
Tagi: Technlogy





Dodaj komentarz